Chapter 2 Cybersecurity and Reliable Websites
Vocabulary
Adware: Software that gathers information regarding a person’s browsing patterns and then displays related advertisements in their Web browser.
Cookies: Allows a website to collect information during the user’s visit to the site.
Cybersecurity: Actions taken to be safe from electronic crime.
Hyperlink: A picture, icon, phrase, or word in an electronic document that when clicked on relocates the user to another section of the document or to another document.
Identity theft: The act of acquiring and fraudulently using account numbers, passwords, or other company or personal information for financial gain.
Malware: Malicious computer software that affects the functioning of a computer. It can gather and send a person’s private information to unauthorized parties over the Internet.
Multi-factor authentication (MFA): Requires two or more steps to identify the user and verify permission to access an electronic device or computer network. Authorization may include a password; a code sent via a text message to the phone number on file; answers to security questions; or identification using the person’s face, retina, or fingerprint.
Phishing: A type of fraud where cybercriminals send emails from a fake website to illegally obtain password information.
Ransomware: Malware that disables the normal operation of a computer or encrypts files until money or other ransom is paid to the person or organization responsible for the malware.
Rootkit: A group of programs that illegally accesses a person’s computer operating system (e.g., Windows) and revises or deletes files and spreads to other computers.
Social engineering: The use of fraud, dishonesty, or psychological manipulation to manipulate people to disclose corporate or personal information, or to take a particular action.
Spoofing: The act of impersonating another person via email or on the Internet in order to gain access to a system or to obtain personal information.
Spyware: Malicious computer software installed on a person’s computer without their knowledge and collects information.
Trojans: Also called trojan horses; malware that misinforms the user about its true intent.
Two-factor authentication (2FA): A verification method that requires a password and another form of verification, such as a fingerprint, a code sent via a text message, phone call, or through a smartphone app.
Uniform Resource Locator (URL): A unique Internet address of a certain website page.
“434” virus: A self-replicating series of commands or a computer program that is illegally planted in a computer program, often to damage or shut down a system or network.
Worms: A type of Trojan horse malware that auto replicates (by itself) between computers.
Introduction
Over the years, Internet usage has increased for both business and personal reasons. Today, banking tasks, purchasing items, researching topics, and viewing one’s electronic health are done using the Internet. With the increased use of the Internet, criminal activity has also increased. Individuals need to protect themselves from criminal activity and ensure websites are legitimate. This chapter discusses cyberattacks, cybersecurity strategies, and the evaluation of websites.
Cyberattacks
Cyberattacks are malicious attempts by scammers to access another’s computer or network system. This can result in theft of personal, medical, and/or financial information. It can result in the loss of money. Cybersecurity includes techniques that focus on preventing, detecting, and responding to cyberattacks.
Malware
Malware includes a wide range of malicious software, including viruses, trojans, ransomware, spyware, worms, rootkit, and adware. Malware can be installed on an electronic device (e.g., cell phone or computer) through the following:
- Phishing: Fraudulent emails or text messages can include malware in attachments that look legitimate. When the user downloads the attachment, the malware loads on the computer system immediately, causing problems or leading to future issues. Malware can also download when the user clicks links or visits websites indicated in the email or text message.
- Networks: Malware from an infected computer can spread through the computers on the network.
- File sharing: Downloading or copying files from other sources can lead to malware on your computer.
- External devices: Plugging in infected flash or external drives can cause malware to infect your computer. Cybercriminals have been known to plant infected flash drives in public locations, hoping someone finds the drive and plugs it into their computer.
- Social networking: Malware transfers onto your computer when the user clicks on infected files and links on social networking sites.
- Apps: Cybercriminals will create apps with malware. Downloading apps from websites can increase the risk of adding malware to your electronic device.
To prevent infecting a device with malware, a person should do the following:
- Only click on links and attachments from legitimate people and companies.
- Plug in flash and external drives that are known to you.
- Use antimalware software on all electronic devices (e.g., computer, cell phone).
- Download apps directly from official app stores, which have verified the legitimacy of the apps.
- Contact the agency’s IT department regarding a suspicious email or attachment.
Opening Attachments From Known People
Many people have had their accounts hacked by cybercriminals. Emails from their account are sent to people in their contact list. Often the emails include infected attachments or links.
If you received an attachment from a known person, you need to ask yourself if it was an expected attachment. If not, then closely look at the email. Are there misspellings or grammatical errors? Is the email address correct? If you are suspicious, it is important to contact the person and ask if they sent the email.
Spoofing
Spoofing is a type of fraud where the cybercriminal pretends to be someone else. The scammer slightly revises a sender’s name, phone number, email address, or website URL. A letter, number, or symbol is typically changed, so the information looks authentic at a quick glance and people assume it is from a trusted source. Cybercriminals manipulate people into believing the communication is real. This leads a person to unintentionally download malware, send money (e.g., bank information, gift card numbers), or provide sensitive information.
Phishing
Phishing (pronounced fishing) is a type of fraud that uses social engineering attacks. The scammer, the person behind the attacks, “baits” a wide range of people, using fake emails, text messages, or fraudulent websites. The scammer poses as a legitimate company or individual and hopes to get personal information (e.g., credit card information and passwords) from unsuspecting victims. The following sections describe several types of phishing and ways to prevent phishing attacks.
Email Phishing
Email phishing is the most common type of phishing. Scammers send emails containing phony hyperlinks, hoping the recipients click on the hyperlink and provide their personal information. Common tactics include posing as an account provider like Google, Amazon, or Microsoft.
To prevent email phishing, a person should ignore emails that contain pictures and little text. The images can hide malware.
For example, Sam received an email from “Amazon.” The email asked Sam to update or verify his personal information and required him to click on a hyperlink. The email looked convincing and pressured him to act “now.” Because the email appeared to be from a legitimate business, Sam clicked on the link. He was sent to a spoofed website that looks legitimate. He was asked for his bank account numbers, banking PINs, passwords, and credit card information.
Spear Phishing
With spear phishing, cybercriminals research and target a few, high-value people. Scammers identify information about people using social media, business websites, and other sites. The attacks are highly customized, looking like legitimate contacts. The criminal may use company logos and other techniques, making the contact look authentic and thus bypassing basic cybersecurity measures. The cybercriminal’s goal is to access a system by gathering your confidential information (e.g., passwords) or to install malware.
To prevent spear phishing, question emails that ask you to share your login and password information or make financial transactions. Your login and password information should never be shared.
What is Spam?
Spam emails are called “junk email” and are usually sent to individuals for advertising purposes. The emails are unsolicited or unwanted by the recipient. Spam emails can contain links for malware.
To prevent spam, a person can do the following:
- Use a spam blocker, though some spam emails may slip through.
- Never open spam email because the sender may use a read receipt that will indicate when you open the email. This may trigger additional emails from the spammer.
- Be careful when entering your email online. Sites can sell your email address to make money. Some resources recommend altering emails posted on public sites to prevent spam bots from copying and using the email. (Bots are software applications that perform texts online that mimic humans.) Alterations can include the following:
- @: “at”
- .gmail: “dotgmail”
- Susie.Brown: Susie(period)Brown
Vishing
Vishing is short for “voice phishing.” Scams occur using voice mail, VoIP (Voice Over Internet Protocol) calls, or phone calls. For example, a scammer may call posing as an IRS agent and request the person’s Social Security number to do an audit.
To prevent vishing attacks, question calls from unusual locations, such as another country, or from blocked numbers. If a call requests personal information, ensure the legitimacy of the caller. Is this type of information usual for this type of call? For instance, IRS agents do not ask for Social Security numbers over the phone.
Smishing
“Smishing” was created using Short Messaging Service (SMS) and phishing. SMS relates to text messaging. Smishing are scams that occur using SMS (text) messages. For instance, you may get a text message indicating a delivery could not be made. You are asked to click the link to take the required action.
To prevent smishing attacks, question the text. Is the text legitimate? For instance, if the text relates to a delivery, are you expecting a delivery? If so, go directly to the delivery service or company website and check the delivery status.
Angular Phishing
With angular phishing, scammers look for unhappy customers. They create fake “business” accounts and respond to the customers, hoping they can obtain personal information. Scammers use social media notification features or direct messaging applications to trick people into acting, such as giving personal information.
To prevent angular phishing attacks, be cautious when you receive notifications indicating you need to act. Do not click on the links. Go to the company’s social media posting to read the response. For direct messages, be careful when receiving a message from a person who rarely uses direct messages. Accounts can be cloned or hacked.
Pharming
Pharming occurs when scammers install a malicious code on your computer, which redirects you to fake websites. The hacker sends malware using an email. The person clicks on the attachment, and the malware is downloaded on the computer. The malware revises the computer’s host files to direct traffic towards a fraudulent website and away from the intended site.
To prevent pharming, review emails and websites for small mistakes, such as a misspelling, strange font, or incorrect content.
Whaling
With whaling, scammers target high-level personnel of companies, such as CEOs. Hackers send text messages or emails that appear to be legitimate but contain malware. The hacker’s goals include stealing administrative credentials and trade secrets.
To prevent whaling attacks, question abnormal requests from people in administrative positions. Be careful not to take the action that is requested. Double-check with the person you believed sent the email to confirm the legitimacy of the email. This can be done by either calling the person or sending a different email to the person.
Preventing Phishing
Individuals can take steps to prevent phishing. When on the job or when using a computer for personal reasons, recognizing and preventing phishing are important.
Sender’s Email Address
Check the email address of the sender. Sometimes the complete email address does not appear and only a display name appears. Using the mouse, hover over the sender’s name. The email address will usually appear.
- Check to see if the email address looks legitimate. Are there misspellings? Are letters inverted or are there other characters?
- Does the domain name match the company sending the email? Are there misspellings? Emails from companies will have their organization’s name in the domain name. For instance, an email from ABC clinic would have a domain name “@ABCClinic.” The email should not be from Gmail or Hotmail.
- If you are unsure about the domain name, use your browser and research the company’s website. Is the domain you are seeing in the email the same indicated on the website?
- If unsure, do not open the email or click links in the email.
Spelling Errors
Check the email subject line and body for spelling errors. If a company is sending you an email, it should be free of spelling errors. Many times, cybercriminals are from non-English speaking countries and typos can be prevalent in those emails.
Addressing the Reader
Read the email and see how it is addressed. Most companies will take the time to personalize emails. Emails that are addressed to you using “Valued Customer” or that just include your last name should be questioned. Also, question emails that are addressed to “Dear” and then your email address. These errors should make you question the email.
Urgent Need to Act
Question emails that create a sense of urgency, for example, messages such as, “You must act now, or your account will be frozen.” Reading these types of messages causes panic, and people may react before they think about safety practices. The sense of urgency and the need to act “now” are red flags. You need to question these emails.
Signature
Review the signature in the email. Most legitimate emails will have contact information in the signature section. Emails with strange signatures or missing contact details should be questioned.
Attachments
Pause and think before clicking on attachments. Did you anticipate receiving the attachment? Would this person send an email? Do not click on attachments you did not anticipate receiving or if you do not know the sender. Opening attachments can cause malware to download onto your computer.
Preventing Identity Theft
Information obtained by cybercriminals can lead to identity theft. Identity theft occurs when a criminal steals another person’s information and uses it without their permission. This personal information, such as credit cards, Social Security number, and health insurance, can be used to create new accounts, make purchases, and commit other types of fraud. As more people use the Internet to pay bills and shop, the amount of identity theft has grown.
When using the Internet, a person should take measures to protect their privacy. The following sections discuss strategies to prevent identity theft.
Creating Strong Passwords
When shopping, banking, or with other Internet activities, sites commonly require people to create accounts and passwords. Having strong, long, and unique passwords is critical for protecting your account from cybercriminals.
When creating passwords, keep the following points in mind:
- Never use your personal information as part of your password. For instance, do not include your street address, your birthdate, or email address. Your username should not be part of your password.
- Never use passwords that contain family names, familiar words found in dictionaries, or patterns, such as “abcabc.”
- Avoid consecutive numbers or letters.
- Use at least 12 characters for a password, though many sites suggest 16 or more characters create a stronger password.
- Use a combination of characters for your password. Use numbers, upper and lowercase letters, and symbols. Placing numbers and symbols in the middle increases the complexity of the password.
- Use different passwords for different accounts. Using the same password is risky if someone finds out your password. Unique passwords increase the security of your online accounts.
- Do not share your passwords with others.
- If asked to change a password, use a different one. A common mistake is to only change one or two characters and leave the rest of the password the same. This does not make complex passwords. Hackers can easily figure out your passwords.
Remembering passwords can be challenging for many people. Some people write down passwords and others use spreadsheets to keep track of their passwords. If someone finds the list of passwords or gets into the spreadsheet, all the accounts are compromised.
Password managers are software that store your passwords and usernames for different sites. The user must enter a master password and then the password manager autofills in your username and password for the site. The master password should be highly secure and complex. This way you can have complex unique passwords for each site (e.g., banking, shopping), but you will just have one password to remember.
Answering Security Questions
Many businesses, like financial institutions, require users to complete security questions. If the user needs to access their account or change their password, they need to answer the security questions. If the answer matches their original answer, then they can access their account or change their password.
Have you ever checked to see what information is available about you on the Internet? What information have you posted on social media sites? With the amount of information available on the Internet about different people, security questions can be hacked by cybercriminals.
Answers may be easily found online for questions like “What high school did you attend?” and “What is your eldest brother’s middle name?” If a cybercriminal determines the answers to a person’s security questions, they can then reset passwords and block the authorized user from the site.
To increase the complexity of your answers to security questions, a person should the following:
- Not be honest when completing the answers to the questions.
- Create an answer that is different from the truth.
- Answer the question with characters that do not spell a word. Think about it as a password.
Using Two-Factor Authentication
Businesses are adding extra security measures, such as two-factor authentication (2FA), before users can gain access to their account or to reset passwords. The 2FA process requires two steps to verify the user. Two-factor authentication can also be considered multi-factor authentication (MFA). MFA requires two or more steps to identify the user.
The 2FA process requires the user to enter a password, along with completing a second step of verification before they can log into their account. The second step of verification may include the following:
- The use of a one-time code, delivered by text message (SMS), email, or phone call. Some businesses give key fobs to users that generate the code to enter.
- The use of biometrics, such as a fingerprint, facial image, or voice recognition.
- The use of hardware tokens. The user must insert a physical token (e.g., USB token) in the device before they can complete the login process.
- Push notifications, which send a message to your phone to either accept/approve or decline/deny the access. This requires the site to have your mobile phone number when the account access is set up.
Internet Safety
Many people use the Internet without considering the potential risks that might be present. From the Internet connection used to the websites visited, it is important to take measures to protect your computer and your personal information from cybercriminals.
Using Public Wi-Fi
Using public Wi-Fi is common for many people. This type of Internet connection must always be considered nonsecure. A person should be cautious of what sites are opened and used when on public Wi-Fi.
Cybercriminals can set up Internet hotspots and name them so that people are misled. For instance, at a local coffee shop, a cybercriminal sets up a hotspot and labels it with the company’s name. Unsuspecting customers who use the hotspot might send information that can be intercepted by cybercriminals.
When using public Wi-Fi, a person should do the following:
- Verify the correct public Wi-Fi from the business.
- Remember the connection is unsecure and refrain from using any secure websites (e.g., a bank account).
- Use a device that is protected by an anti-malware product.
Understanding Web Addresses
When browsing online, a person should only open legitimate websites. Understanding the Uniform Resource Locator (URL) structure is important when safely browsing the web.
The following address is for the Wisconsin Department of Health Services. The parts of the URL are labeled and described in the following section (Figure 1).
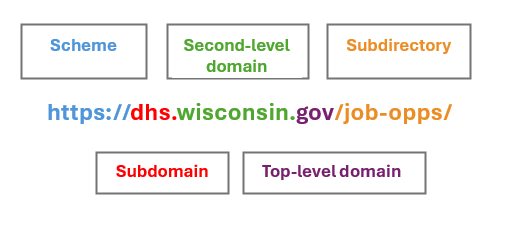
Parts of a website are as follows:
- Scheme: Tells the web service which protocol to use for the website. Years ago, Hypertext Transfer Protocol (HTTP) was common, but today Hypertext Transfer Protocol Secure (HTTPS) is replacing it because it is more secure.
HTTPS tells the web browser to encrypt any information the user enters on the page. This prevents cybercriminals from accessing it. Many websites use a padlock to the left of the website address, and HTTPS is not visible (Figure 2). If you copy and paste the website, you will see it is present (Figure 3).
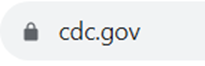

Example: A website asks for your credit card number to pay for a purchase. If you are on a HTTPS site, you will either see a padlock in the URL bar or HTTPS:// before the company’s website address. With HTTPS, your information will be encrypted during the transfer, securing the data.
When entering personal information online, a person should always ensure the site is secure. The website should either have the padlock or the HTTPS:// in front of the website in the URL bar. Do not enter personal information on non-secure sites. Be cautious of any site that looks suspicious. Hackers have been known to create sites using padlock icons and websites with misspelled HTTPS. Some web browsers will indicate if the site is not secure. This indication may appear near the URL bar.
- Subdomain: Tells the browser the specific page of the website to open.
- Second-level domain: Indicates the name of the website. Many times businesses will use their name as the second-level domain. It is important to make sure the business name is spelled correctly. Cybercriminals will frequently clone sites and alter the business name by dropping a letter, adding a letter, or switching around letters.
- Top-level domain: Shows the type of organization the website is from (Table 1).
- Subdirectory: Can also be considered a subfolder and identifies the specific section of the website the user is on.
| Type of Organization | Top-level Domain | Example |
|---|---|---|
| U.S. commercial entity | .com | https://www.culvers.com/ |
| Academic institution | .edu | https://www.cvtc.edu/ |
| Governmental agency | .gov | https://www.whitehouse.gov/ |
| U.S. military | .mil | https://www.army.mil/ |
| Organization (open to anyone to register and use this domain) | .org | https://www.aama-ntl.org/ |
| Network (open to anyone to register and use this domain) | .net | https://www.wsma.net/ |
Additional Internet Safety Tips
When searching the web, it is important to realize that search results on the first page may be safer to view than those on subsequent pages. Most search engines prioritize websites that are most relevant to the terms searched. Often websites on subsequent pages may contain malware.
Web content filtering is becoming more popular for homes and businesses. Web content filtering can prevent the user from seeing malicious content, such as advertisements or websites. For personal use, these filters can restrict what is viewed and the amount of time a certain site is used. For businesses, web content filtering is used to restrict access from certain content. It may restrict unlawful content and content that reduces employee productivity. For instance, allowing access to shopping and social media websites can decrease productivity.
Evaluating Health Websites
When researching health-related topics online, many times a large amount of search results appear. It can be difficult to identify reliable information. When looking for reliable information, a person must consider a number of factors.
Identifying Reliable Websites
When evaluating a website, the following eight factors should be considered:
- Who owns or sponsors the website? Knowing who owns or sponsors the site can provide insight on the goal or mission of the site. Looking at the website (e.g., .gov or .edu) can provide clues.
- Who sponsors or pays for the website? Many sites contain paid advertising. It is important to confirm information found on websites that contain advertising.
- What is the purpose of the website? Typically, websites either are designed to inform or educate the public or they might be selling a product or service. Usually, finding sites that educate or inform can be more reliable.
- Who is the author of the content? Check to see the person’s credentials and if they are an expert in their field. Checking the mission of the organization the person represents can also be helpful. Where does the person work and what are the organization’s goals? Who reviews the content? What are their credentials? Information may be more trustworthy if the person has related credentials. For instance, medical information written by a medical doctor may be more reliable than medical information written by someone with no credentials. Usually, health information is reviewed by others.
- When was the content written, reviewed, and updated? Usually, the date the information is written, reviewed, or updated is either found at the beginning or at the end of the article. Current information is ideal.
- Does the website have contact information? Many trustworthy websites contain email addresses, mailing addresses, and/or phone numbers. These are usually available in the “Contact Us” or “About Us” page.
- Does the website indicate their privacy policy and is the viewer’s privacy protected? Many websites track the activity of users and sell the data. Data can be obtained from users if they complete “subscribe” information or complete “become a member” pages. If “cookies” are used, a person’s information may not be private. Usually, a user can select to disable the use of cookies if a person is concerned about the use of their information. Usually, the “Our Policies” or “Privacy Policy” are located at the bottom of the page. Reading the website’s policies before providing personal information can increase one’s online safety.
- Does the website offer easy solutions for health problems? Websites that promise cures should be viewed with caution. The user should use other reliable websites to verify information seen on “suspicious” websites.
Online Sites for Health Information
The following are reliable sites for health information:
- Academy of Family Physicians: Provides information on diseases, conditions, prevention, and wellness. Website: https://familydoctor.org/
- American Diabetes Association: Provides information on living with diabetes. Website: https://diabetes.org/
- American Heart Association: Provides information on healthy living and health-related topics. Website: https://www.heart.org/
- American Lung Association: Provides information on lung health and diseases, smoking cessation, and research. Website: https://www.lung.org/
- American Medical Association: Provides information for physicians and the public about health care advocacy, health topics, and practice management. Website: https://www.ama-assn.org/
- Centers for Disease Control and Prevention (CDC): Provides information on health topics, traveler’s health, workplace safety, and environmental health. Website: https://www.cdc.gov/
- Cleveland Clinic: Provides access to a health library, which includes information on diseases and procedures. Website: https://my.clevelandclinic.org/
- MedlinePlus: Provides information on health topics, medications, supplements, medical tests, and genetics. Website: https://medlineplus.gov/
- Mayo Clinic: Provides symptom checker and information on clinical trials and support groups, along with health information about diseases and conditions. Website: https://www.mayoclinic.org/diseases-conditions
- National Institutes for Health: Provides health information on a variety of topics, along with links to other .gov sites. Website: https://www.nih.gov/
- National Library of Medicine: Provides information on clinical trials and health information. Website: https://www.nlm.nih.gov/
- RxList: Provides information on prescription medications and supplements. Website: https://www.rxlist.com/
- Substance Abuse and Mental Health Services Administration: Provides information on substance abuse and mental health. Website: https://www.samhsa.gov/
- WebMD: Provides information on conditions, drugs, supplements, and wellness. Also includes a symptom checker. Website: https://www.webmd.com/
Health Apps
Health applications (“apps”) can be installed on smartphones and other mobile devices. Apps are available for health, medication, diet, and exercise information. When downloading an app, it usually asks for the user’s information, including location, email address, and contact information. It is important to ensure the private information requested is relevant to the app. Knowing how the company will use the information is also important to the user.
Health Information on Social Media
When reading health information on social media sites, such as Facebook or X (previously known as Twitter), it is critical to check the sponsor’s website. Usually, the website is located on the social media site. Some social media sites also use a symbol to indicate verified accounts. Linking to an organization’s social media account by going through their website is helpful.
Learning Activities
Cybersecurity and Reliable Websites – Flash Cards
Application Exercise 1
Based on what you have learned, what parts of this email may indicate that it is a phishing email.
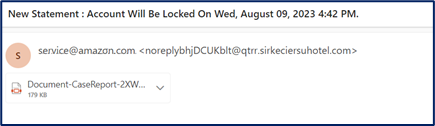 ANSWERS: Sender’s email address does not look legitimate. Creates a sense of urgency. The email has an attachment.
ANSWERS: Sender’s email address does not look legitimate. Creates a sense of urgency. The email has an attachment.
Application Exercise 2
- Select a health topic, such as a disease.
- Research the topic using the Internet.
- Evaluate two websites for reliable information. For each website:
-
- Summarize your findings for each of the eight factors.
- Discuss whether the website is reliable or not reliable.
- List the website evaluated.
Actions taken to be safe from electronic crime.
Malicious computer software that affects the functioning of a computer. It can gather and send a person’s private information to unauthorized parties over the Internet.
Also called trojan horses; malware that misinforms the user about its true intent.
Malware that disables the normal operation of a computer or encrypts files until money or other ransom is paid to the person or organization responsible for the malware.
Malicious computer software installed on a person’s computer without their knowledge and collects information.
A type of Trojan horse malware that auto replicates (by itself) between computers.
A group of programs that illegally accesses a person’s computer operating system (e.g., Windows) and revises or delete files and spreads to other computers.
Software that gathers information regarding a person’s browsing patterns and then displays related advertisements in their Web browser.
A type of fraud where cybercriminals send e-mails from a fake website to illegally obtain password information.
The act of impersonating another person via email or on the Internet in order to gain access to a system or to obtain personal information.
The use of fraud, dishonesty, or psychological manipulation to manipulate people to disclose corporate or personal information, or to take a particular action.
A picture, icon, phrase, or word in an electronic document that when clicked on, relocates the user to another section of the document or to another document.
The act of acquiring and fraudulently using account numbers, passwords, or other company or personal information for financial gain.
A verification method that requires a password and another form of verification, such as a fingerprint, a code sent via a text message, phone call, or through a smartphone app.
Requires two or more steps to identify the user and verify permission to access an electronic device or computer network. Authorization may include a password, a code sent via a text message to the phone number on file, answers to security questions, or identification using the person’s face, retina, or fingerprint.
A unique Internet address of a certain website page.
Allows a website to collect information during the user’s visit to the site.

